The Open Worldwide Application Security Project (OWASP) has released its latest update on the Top 10 most critical web application security risks.
Drawing on both real-world breaches and vulnerabilities uncovered in global cybersecurity assessments, the report ranks these risks based on their impact, exploitability, and prevalence as they have evolved from their previous report published in 2021.
Alongside data collated from over 2.8 million applications submitted by cybersecurity vendors and researchers, the report is also informed by a survey undertaken by application security and development practitioners in order to account for significant risks that may have been unrepresented by the data.
The top 10 risks identified in the new 2025 report are categorised as follows:
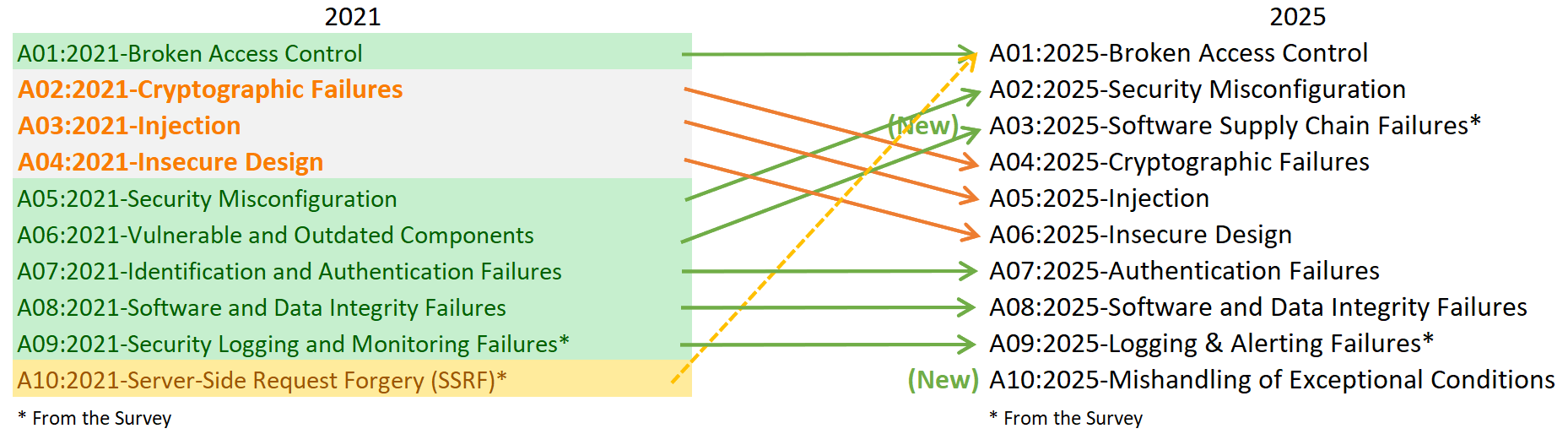
A01 Broken Access Control
Access control ensures that sensitive data and resources cannot be accessed by users who are not authorised to view or use them. Failure to properly implement these controls can result in the unauthorised disclosure of information, the modification and destruction of data, and/or allowing users to execute business functions beyond the intended scope of a user’s permissions.
Control measures include implementing the principle of least privilege as a standard framework, and locking accounts or introducing delays after repeated failed login attempts.
A02 Security Misconfiguration
Security misconfiguration occurs when systems, applications, or cloud services are left insecure due to incorrect or incomplete security settings.
Organisations should regularly review existing cyber protections for their effectiveness, minimise attack surfaces by disabling any unnecessary features and services, and apply vendor security patches promptly to avoid prolonged exposure to known vulnerabilities.
A03 Software Supply Chain Issues
Software supply chain risks arise when attackers compromise the process of building, distributing, or updating third-party software. Attackers may exploit weaknesses in the components of software, such as in respect of zero-day vulnerabilities.
Organisations should monitor reputable sources such as CVE: Common Vulnerabilities and Exposures, and avoid the use of software that has reached End of Support (EoS) status.
A04 Cryptographic Failures
Cryptographic failures refer to an application’s failure to protect data through secure encryption, allowing unauthorised parties to access sensitive information.
Organisations should ensure that both data at rest and in transit is encrypted, avoid the use of deprecated and therefore vulnerable cryptographic functions, and adopt a data retention policy to prevent the unnecessary storage of sensitive data.
A05 Injection
An injection, such as SQL or XSS, is a vulnerability that allows an attacker to insert malicious code and/or commands into a webpage’s input fields. Injections attacks can occur, for example, in search bars and comments sections. Where successful, attackers can steal sensitive data and take control of applications.
The most common preventative measure against injection attacks is to validate and sanitise user message fields, blocking the input of known characters and patterns commonly used to insert malicious code.
A06 Insecure Design
Insecure design refers to flaws in the architecture and planning of an application, such as the absence of threat modelling, potentially leading to exploitable security weaknesses.
Security should be integrated into all stages of software development to ensure that systems are designed to withstand known attack methods.
A07 Authentication Failures
Authentication failures occur when systems do not reliably verify user identities or enforce strong authentication practices, allowing attackers to impersonate users and gain unauthorised access to data and systems.
Organisations should implement multi-factor authentication, enforce strong password policies, and limit or increasingly delay failed login attempts.
A08 Software and Data Integrity Failures
Software and data integrity failures occur when infrastructure does not protect against the use of invalid or untrusted code, such as through the installation of malicious software.
Preventative measures include using digital signatures to verify that software or data has come from the expected source, and implementing application allow-listing (also referred to as application whitelisting) supported by code signing.
A09 Logging & Alerting Failures
Insufficient logging and alerting of suspicious activities can delay the detection of security breaches and hinder incident response, allowing attackers to operate undetected and for prolonged periods of time.
Where possible, organisations should log and monitor critical events in real time, and ensure suspicious events generate alerts for the relevant personnel or systems.
A10 Mishandling of Exceptional Conditions
Mishandling of exceptional conditions refers to the failure in managing unexpected states and errors of systems, which can lead to system crashes, information leakage, and exploitable conditions.
Improved resilience is achieved by aligning cybersecurity measures with the organisation’s risk profile and establishing robust incident response plans to enable a swift, coordinated action during security events.
The full publication can be viewed here.
The OWASP Top 10 highlights how cyber threats continue evolve and reinforces the importance of implementing a proactive, strategic approach to navigating the cyber landscape.
For further information and support, please get in touch.
Whilst care has been taken in the production of this article and the information contained within it has been obtained from sources that Griffiths & Armour, an Aon company believes to be reliable, Griffiths & Armour, an Aon company does not warrant, represent or guarantee the accuracy, adequacy, completeness or fitness for any purpose of the article or any part of it and can accept no liability for any loss incurred in any way whatsoever by any person who may rely on it. In any case any recipient shall be entirely responsible for the use to which it puts this article.This article has been compiled using information available to us up to 17 November 2025







